I read an article titled Frequent password changes are the enemy of security which I find misleading and missing the point.
In this article, Carnegie Mellon University professor Lorrie Cranor, who became chief technologist at FTC challenges FTC’s advice
FTC’s advice: Encourage your loved ones to change passwords often, making them long, strong, and unique.
Cranor finds this advice problematic and the reason is
Cranor: growing body of research suggests that frequent password changes make security worse.
Then she goes on to say that when people are forced to change their password, they use a pattern to transform it, for e.g. tarheels#1 ==> tArheels#1 ==> taRheels#1 ==> etc, and researchers were able to predict such changes with great accuracy.
I don’t understand how changing a password from tarheels#1 to tArheels#1 by using a predictable transformation can make things worse or make it more susceptible to cracking than not changing the password. Both are vulnerable.
me: WITH WEAK PASSWORDS LIKE tarheels#1 AND THEIR TRANSFORMATIONS, IT DOESN’T MATTER IF YOU CHANGE THE PASSWORD FREQUENTLY OR NEVER CHANGE IT — HACKERS WILL BREAK INTO THE ACCOUNT IN EITHER CASE.
On the other hand, changing your password from g4xRAgnAJE3Y#tj via a simple transformation to 4xRAgnAJE3Y#tjg, doesn’t make it more vulnerable or make security any worse. Neither does it provide much benefit.
There is nothing wrong in FTC’c advice "change passwords often, making them long, strong, and unique", the important part being long, strong, and unique. A password like tarheels#1 is not long and definitely not strong.
A randomly generated password like g4xRAgnAJE3Y#tj conforms to FTC’s advice of making them long and strong.
me: with such randomly generated passwords, it doesn’t matter if you never change them or change them frequently — you are protected. If you are not asked to change passwords, you don’t need to do anything but if you are forced to change them, do so.
Professor Cranor says
Cranor: I’m happy to report that for two of my six government passwords, I don’t have to change them anymore
I hope her password is not tarheels#1 or similar, as her account may have been breached long back.
So, the conclusion based on the research into user behavior should not be "changing passwords frequently makes security worse" (which is not true) but "PLEASE DON’T USE WEAK PASSWORDS LIKE tarheels#1" — when people follow that advice and choose strong, random passwords, it doesn’t matter much how frequently they are changed.
But it is good to check security related news periodically in case some sites get breached. If this happens, you can change the password for the site from the current long, strong, and unique (I hope you have such a password) to another long, strong, and unique (unrelated) password.
Note that long, strong, and unique passwords won’t help if the site is using poor security practices and gets hacked. Unfortunately, this is not a rare occurrence, a recent example being that of LinkedIn. If this happens, you get more protection if
- a) you use a password like g4xRAgnAJE3Y#tj than tarheels#1. It will take much longer time (probably years or never) for the hackers to take the exfiltrated data and recover your password. They will go after people with weak passwords like tarheels#1 as they are easier (relatively speaking) to recover.
- b) and most importantly, you don’t use the same password on other sites.
In 2016 (and even earlier), if a website accepts weak passwords like tarheels#1, you should avoid using that site, unless it is one where you and your friends enter their predictions on who is going to win which ball game. If it is a bank, credit card issuer, e-commerce site, brokerage house (all highly unlikely), it tells a lot about their security practices (or lack thereof) and you are better of closing the account and switching to a provider that takes security seriously. If you cannot change providers, then your best bet (in addition to using long, strong, unique passwords) is to have a chat with the people in charge of security and express your concerns. If it is an employer and the site is on the internet (as opposed to intranet where you need to use a vpn), talk to your colleagues and collectively approach management for a security review/audit. Note that while intranet access with vpn provides some protection, you are still vulnerable to attacks from inside the organization.
Most sites (that have sensitive user info, like banks) specify password complexity requirements and show password strength meters and will not allow you to enter weak, predictable or dictionary-based passwords. Many websites store the hash of last 3 passwords and can check if you are reusing the passwords (for e.g. cycling thru 3 passwords). When you provide a new password, they can compute the hash of hundreds of transformations of that password to see if it matches an existing hash and if so, will not accept your new password.
So, I hope I have convinced readers that the objection raised by Carnegie Mellon University professor Lorrie Cranor to FTC recommendation of "change passwords often, making them long, strong, and unique" is not valid or useful as it is based on people ignoring FTC’s advice and choosing passwords like tarheels#1.
The main problem with FTC’s recommendation is that it is not easy to follow: choosing long, strong and unique passwords for each of your sites is difficult enough, not to mention changing them frequently, if required to do so.
So, what is the solution?
In my opinion, for most people, and more so for older folks, if you can remember a password, then it is quite likely not a good password. Even if some people (a minority) say this is not true for them, all would agree that it is impossible to remember 5 or 6 passwords which have no relationship to each other. You may ask "Why do you need 5 or 6 or many more passwords?" Many make the mistake of using same password on multiple sites, mainly because it is not easy to remember many passwords and this is a bad idea. When a site that you use is breached by attackers (unfortunately this is not a rare occurrence), then your other sites that use the same password are also vulnerable.
Some points to consider:
- For reasons mentioned earlier, you should not have the same password on more than 1 site
- Most people access multiple sites like banks, credit cards issuers, mortgage accounts, e-commerce providers, brokerage accounts, insurance cos and so most people need at least 6 or more passwords (typically 15 or more)
- passwords should be long, strong and randomly generated
- changing passwords should be very easy and preferably automated
- writing passwords down on a piece of paper is not a good idea
- storing them in an un-encrypted text file is not a good idea as is not only vulnerable but you can lose this info if there is a disk crash or if the laptop is stolen.
- manually entering passwords from a piece of paper or text file is not a good idea at it is cumbersome, error-prone, slow, cannot be done in a public place and most importantly, key loggers can capture them. Using virtual keyboard every time to enter long passwords with lower case, upper case, number and special characters is cumbersome and error-prone and you can get locked out if you enter the password wrong a few times. Entering such passwords on mobile devices is much more difficult as you have to hunt and peck.
- if you and your spouse access accounts from their own laptops, keeping passwords in sync when one person changes it can get tiresome; if the other person uses the old password, the account can get locked out.
- if you need to access your bank site while on vacation (or from your parents’ place) and you don’t have your laptop or the piece of paper with the passwords, you are out of luck.
The only solution is to use a password manager. I use and recommend Lastpass — they have a free version and premium version that costs $1 a month. There are others like dashlane, 1password. You can check all the password managers recommended by security experts and pick one that you like.
To give an example of how password managers make changing passwords easy:
me: I don’t know my twitter password, nor the passwords for any of the sites I use, except that they are long, strong and unique. I recently changed my twitter password (due to reports of hacks) — all I had to do was click on a link and my password was changed in a few seconds. I don’t know the new password and I like to keep it that way!
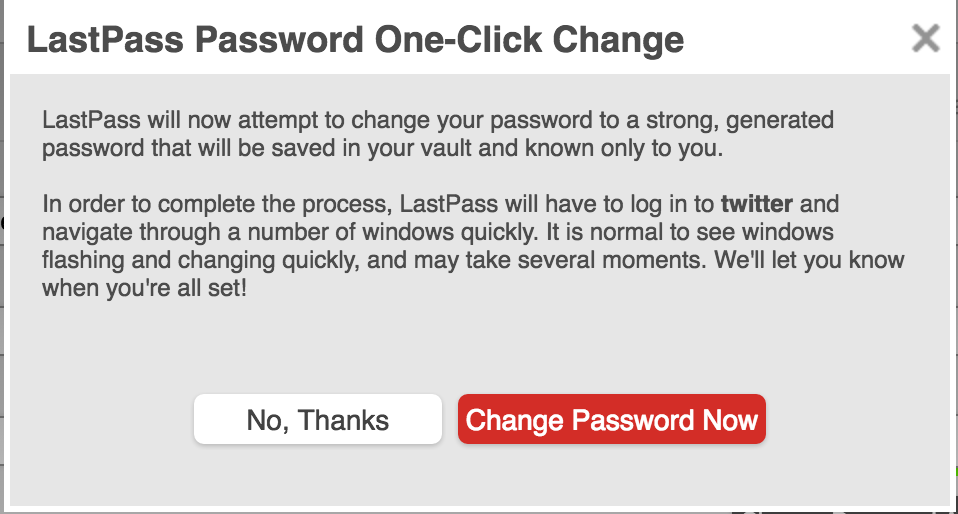
Lastpass provides this auto-password-change feature on about 75 sites.
With lastpass (and other similar password managers), you just need to remember one long, very strong master password which can be based on a quirky passphrase that you can remember. You can enable multi-factor authentication (either using software or a hardware key like yubikey) which can protect you even if your master password is compromised; you generate one-time passwords (before going on vacation) for use on computers that don’t belong to you.
In summary, FTC’s advice "Encourage your loved ones to change passwords often, making them long, strong, and unique" is valid. However, you cannot keep these passwords in your head or on a piece of paper and therefore you need to use a password manager. If you are required by site policy to change passwords, or if a site gets hacked, you can use the "generate password" feature of the password manager to generate a new long, strong password. For many well known sites like facebook, twitter, dropbox, amazon and many more, you can automatically change the password in a few seconds by selecting the "Auto Change Password" link in the password manager. Now, that isn’t too difficult, is it?
